when a password #Pepper is applied, it doesn't matter whether the original password (plaintext) is a weak password. It will be gain the right "entropy" which is the most important quality for a password at the end of the day.
The next step after #peppering a password is to pass it to a function that will salt and hash it e.g. Bcrypt, Scrypt or Argon2
See this article for more info: blog.ircmaxell.com/2015/03/securi…
See: php.net/manual/en/func…
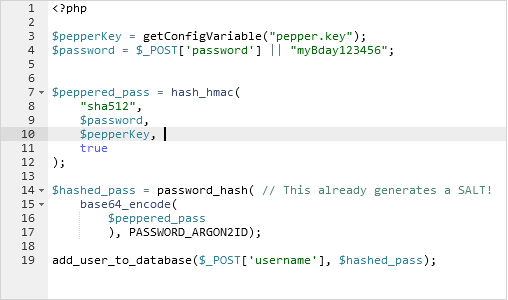
So how do we #pepper passwords correctly you might ask ?
Like so:
Finally, i will like to dispel certain user password entry myths
See this article: dev.to/nathilia_pierc…
One last thing, when creating a #Pepper hashing algos 'sha384' & 'sha512' are truly acceptable.
THE END!