climateaudit.org/2017/09/02/ema…
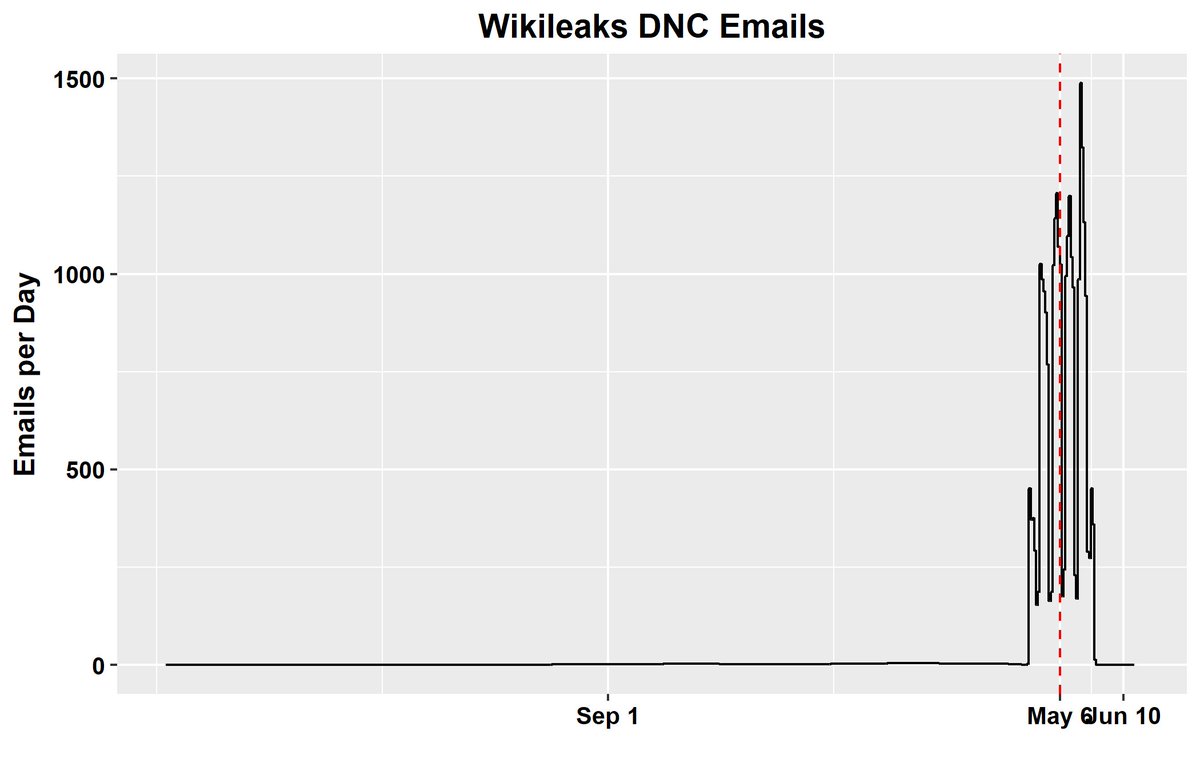




climateaudit.org/2018/03/24/att….
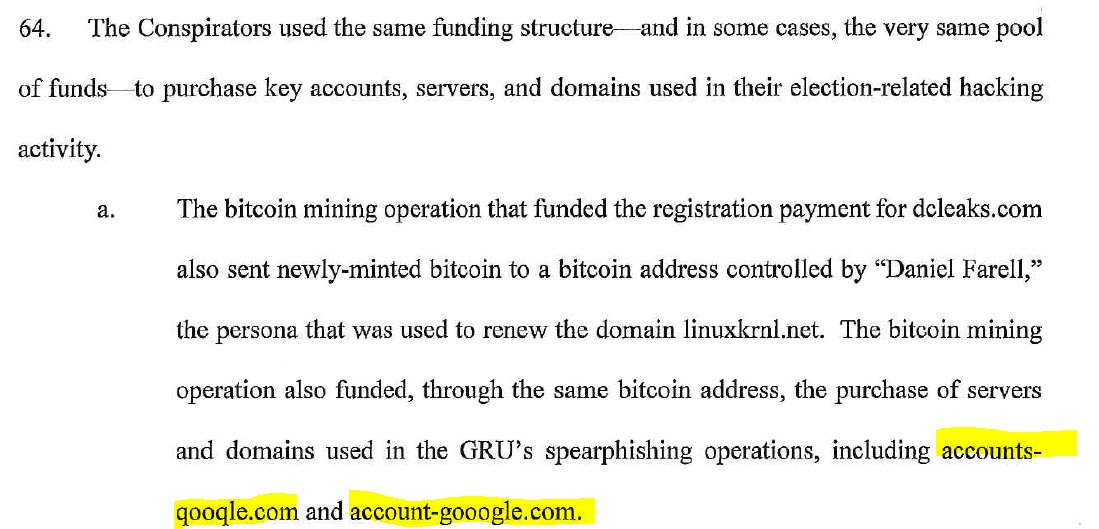
I analysed two typosquatting domains: accoounts-google[.]com and url.googlesetting[.]com used in attribution by SecureWorks. Two similar domain names mentioned in Indictment.

WHAT IF actblues[.]com was major purpose of X-Agent hackers? Elaborate malware not needed to phish emails
docquery.fec.gov/cgi-bin/forms/…