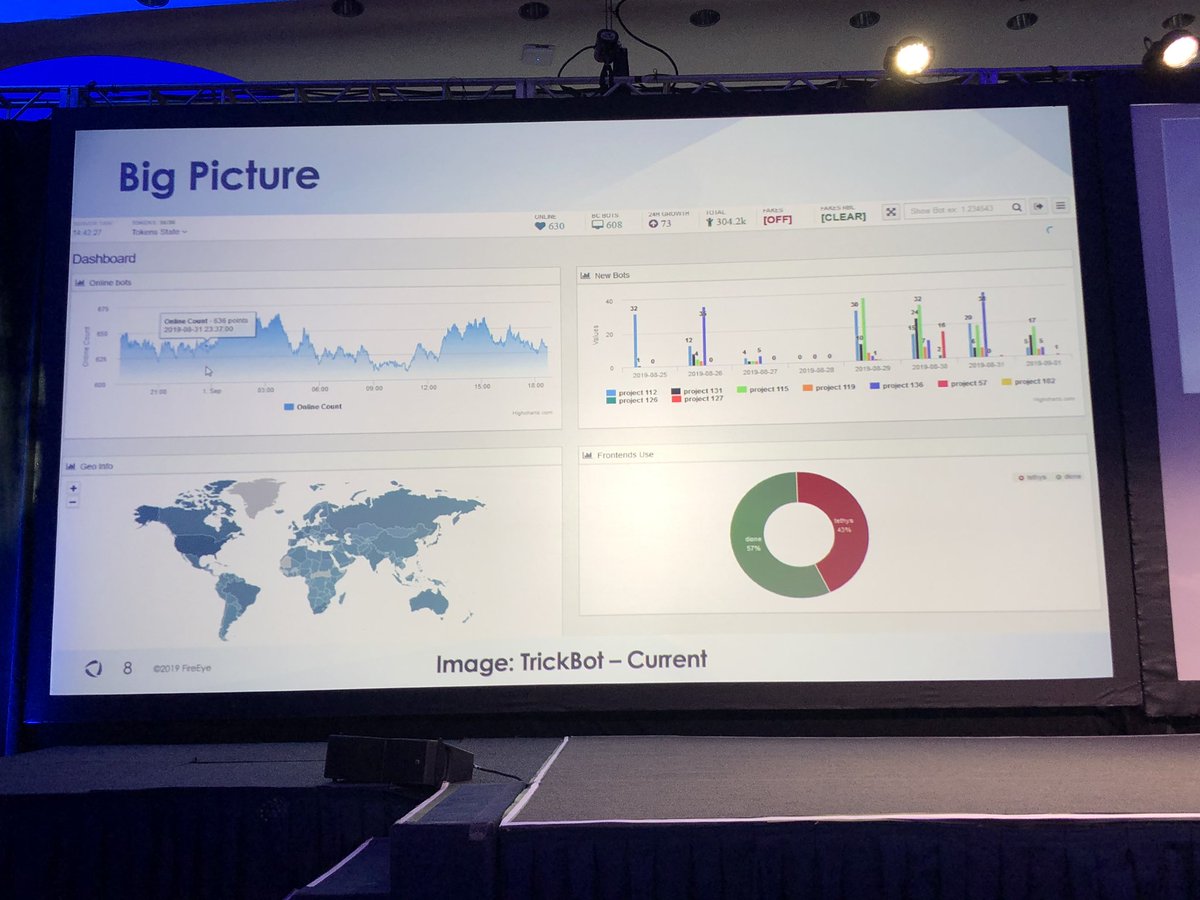
fireeye.com/blog/threat-re…
Remember the MESSAGETAP malware?
fireeye.com/blog/threat-re…
I've never seen/analyzed MIPs malware before. I assume payload is custom.
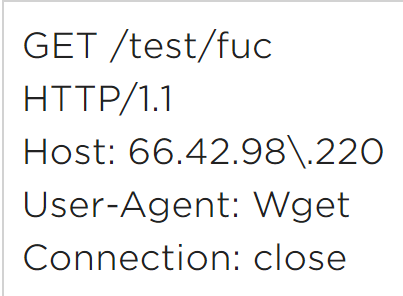
The ManageEngine exploitation was ~3 days from POC release to weaponization. Why did it take ~10 days to attempt exploitation of Citrix ADC (for recon) and ~20 days to exploit it with an actual payload?